In the sprawling digital landscape of the 21st century, where data is the new currency, securing the pathways through which this information travels has never been more critical. Every day, billions of users share personal details, credit card numbers, and confidential messages online, trusting that their data will remain private. The cornerstone of this trust is a technology known as SSL/TLS. But what exactly is it? And how does it work its magic?
This comprehensive guide will demystify the world of SSL/TLS certificates. We’ll explore everything from the fundamental encryption concepts and the intricate process of a TLS handshake to the various types of certificates available and their profound impact on user trust, SEO, and overall web security.
Part 1: The Core Concepts – How SSL/TLS Works
Before we can appreciate the different types of SSL certificates, we must first understand the foundational technology that powers them. At its heart, SSL (Secure Sockets Layer) and its modern, more secure successor, TLS (Transport Layer Security), are cryptographic protocols designed to provide secure communication over a computer network. When you see a padlock icon and “HTTPS” in your browser’s address bar, you’re seeing TLS in action.
The Magic of Encryption: Asymmetric vs. Symmetric
SSL/TLS uses a clever combination of two encryption methods to create a secure channel:
- Asymmetric Encryption (Public Key Cryptography): This method uses a pair of keys: a public key and a private key. The public key is shared openly and can be used by anyone to encrypt data. However, that data can only be decrypted by the corresponding private key, which is kept secret on the server. This is crucial for securely establishing the initial connection.
- Symmetric Encryption: This method uses a single, shared key to both encrypt and decrypt information. It’s much faster and more efficient than asymmetric encryption, making it ideal for the ongoing data transfer once a secure connection is established.
A Deep Dive into the TLS Handshake
The process of establishing a secure connection is called the TLS handshake. It’s a complex sequence of back-and-forth messages between your browser (the client) and the web server. While it happens in milliseconds, a lot is going on behind the scenes. Here’s a simplified breakdown of the key steps:
- Client Hello: Your browser initiates the handshake by sending a “Client Hello” message to the server. This message includes the TLS version it supports, a list of available cipher suites (encryption algorithms), and a random string of bytes called the “client random.”
- Server Hello: The server responds with a “Server Hello” message. It confirms the TLS version and the cipher suite it has chosen from the client’s list. It also sends its SSL certificate and another random string of bytes, the “server random.”
- Authentication: The browser now verifies the server’s SSL certificate. It checks that the certificate was issued by a trusted Certificate Authority (CA) and that it hasn’t expired or been revoked. This step is vital for ensuring the server is who it claims to be.
- Premaster Secret: The browser generates another random string of data, the “premaster secret,” encrypts it using the server’s public key (from the SSL certificate), and sends it to the server. Only the server, with its private key, can decrypt this.
- Session Keys Created: Both the client and the server now use the “client random,” “server random,” and the “premaster secret” to independently generate the same set of symmetric session keys. Since they are created from the same ingredients, they will be identical.
- Secure Communication Begins: The handshake is complete. From this point on, all communication between the browser and the server is encrypted and decrypted using the newly created session keys.
The Role of the Certificate Authority (CA): The Pillars of Trust
How does your browser know it can trust an SSL certificate? This is where Certificate Authorities (CAs) come in. A CA is a trusted third-party organization that validates the identity of entities (like websites or companies) and issues digital certificates.
Browsers and operating systems have a pre-installed list of trusted root CAs. When a browser receives an SSL certificate, it checks if the certificate’s signature can be traced back to one of these trusted roots. If it can, the certificate is considered valid and authentic. This “chain of trust” is fundamental to the entire web security ecosystem.
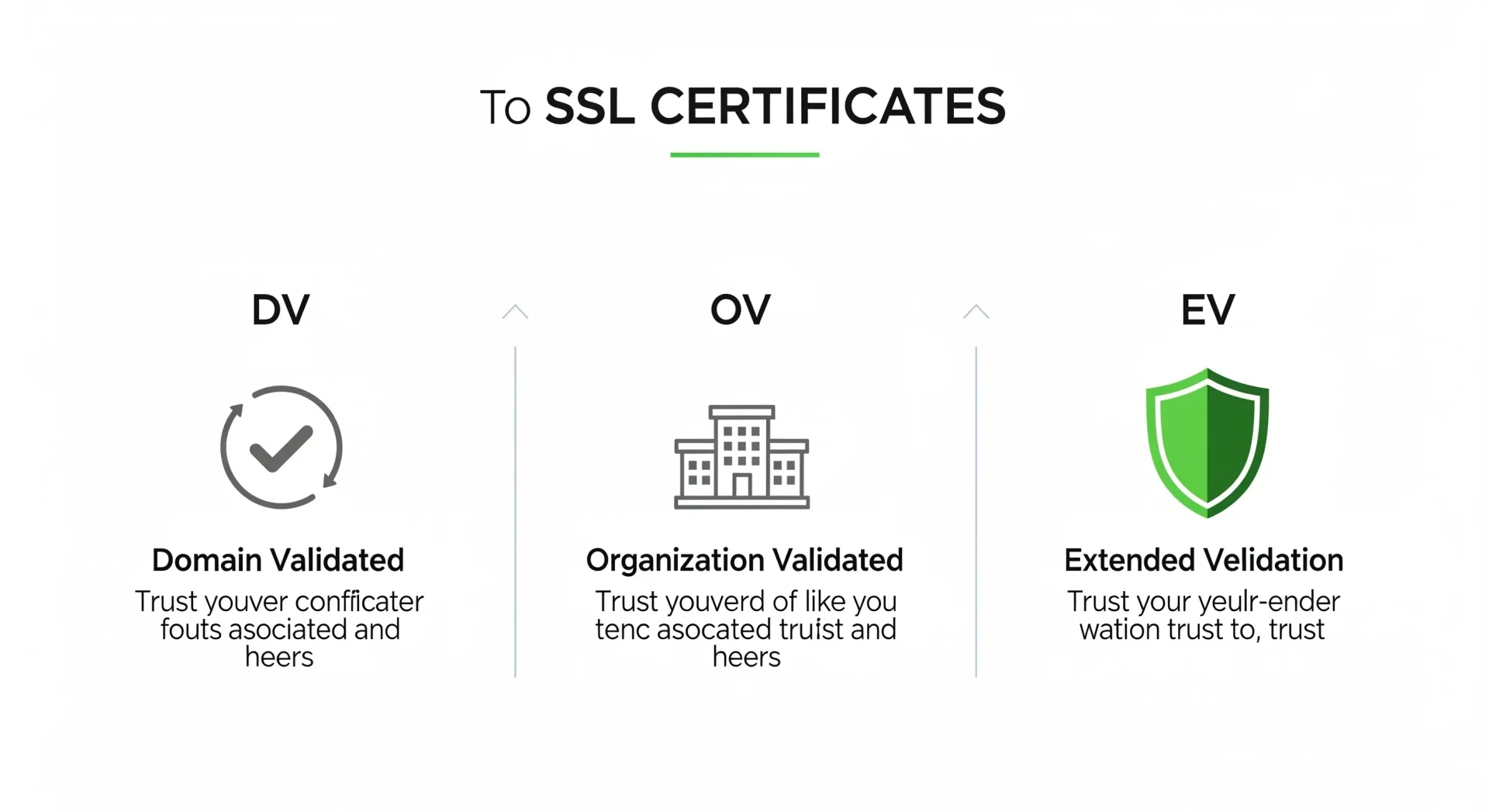
Part 2: A Guide to SSL Certificate Types
Not all SSL certificates are created equal. They differ based on the level of validation performed by the CA and the number of domains they are designed to protect. Choosing the right one depends on your website’s needs and your organization’s goals.
Validation Levels: How Much Trust Do You Need?
- Domain Validated (DV) SSL: This is the most basic and common type of SSL certificate. The CA only verifies that the applicant controls the domain name, usually via an email or DNS record check. DV certificates provide full encryption but offer minimal identity assurance.
- Best for: Blogs, personal websites, and small businesses that don’t handle sensitive user data.
- Features: Issued in minutes, shows HTTPS and the padlock icon.
- Organization Validated (OV) SSL: This certificate involves a more rigorous validation process. The CA vets the organization’s identity, verifying its legal name, location, and other business details. This provides a higher level of trust.
- Best for: Public-facing businesses, non-profits, and organizations that want to display verified business information.
- Features: Displays company information in the certificate details, enhancing user confidence.
- Extended Validation (EV) SSL: This offers the highest level of trust and security. The CA conducts a thorough and strict vetting process according to standards set by the CA/Browser Forum. In the past, EV certificates would activate a green address bar with the company’s name, though most modern browsers now display this information in the certificate details.
- Best for: E-commerce sites, financial institutions, and any website handling sensitive data like credit card payments or health records.
- Features: Provides the strongest signal of trust and legitimacy to visitors.
Domain Coverage: Securing Your Digital Footprint
- Single-Domain SSL: As the name implies, this certificate secures a single fully qualified domain name (e.g.,
www.ded9.com). It will not cover any other subdomains. - Wildcard SSL: A Wildcard certificate secures a single domain and an unlimited number of its first-level subdomains. It is denoted by an asterisk in the common name (e.g.,
*.ded9.com). This one certificate could securewww.ded9.com,blog.ded9.com,shop.ded9.com, and so on. - Multi-Domain (SAN) SSL: A Subject Alternative Name (SAN) certificate allows you to secure multiple, distinct domain names with a single certificate. For example, you could secure
ded9.com,anothersite.org, andmy-new-app.ioall under one SAN certificate. These are also sometimes called Unified Communications Certificates (UCC).
Part 3: The Tangible Benefits of Implementing SSL
Installing an SSL certificate is no longer an optional extra; it’s a fundamental requirement for any modern website. The benefits extend far beyond just encryption.
Fortifying Security and Protecting Data
The primary benefit is, of course, security. By encrypting data in transit, SSL/TLS protects sensitive information from eavesdroppers and man-in-the-middle attacks. This is non-negotiable for any site that has a login form, collects personal information, or processes payments.
Building User Trust: The Power of the Padlock
The padlock icon has become a universal symbol of safety and trust for internet users. Modern browsers actively warn users when they visit a non-HTTPS site, often displaying a “Not Secure” message. Lacking an SSL certificate can deter visitors, increase bounce rates, and damage your brand’s reputation. A secure connection reassures users that you take their privacy seriously, encouraging them to engage with your site.
Boosting SEO: Why Google Rewards Secure Websites
In 2014, Google officially announced that HTTPS is a ranking signal. While it may be a lightweight signal, having a secure website gives you a competitive advantage in search engine results pages (SERPs). Furthermore, security is a core component of Google’s Page Experience signals. A secure website provides a better user experience, which is what search engines aim to reward.
Part 4: Practical Guide – Installation and Troubleshooting
Once you’ve chosen a certificate, you need to install it on your web server.
Step-by-Step Installation (General Overview)
While the exact steps vary depending on your hosting provider and web server (like Apache, Nginx, or IIS), the general process is as follows:
- Generate a CSR (Certificate Signing Request): This is an encrypted block of text containing your domain name and public key. You generate it on your server.
- Purchase/Request the Certificate: You submit the CSR to your chosen Certificate Authority. They will perform the validation process based on the certificate type.
- Receive and Install Certificate Files: The CA will send you the certificate files (usually a
.crtfile and a CA bundle file). You then upload these files to your server via your hosting control panel (like cPanel) or command line. - Force HTTPS: After installation, you must configure your website to redirect all HTTP traffic to HTTPS. This ensures all visitors are on the secure version of your site. This is typically done by editing the
.htaccessfile on your server. - Check for Mixed Content: Ensure that all resources on your site (images, scripts, stylesheets) are loaded over HTTPS. If some elements load over HTTP, browsers will show a “mixed content” warning, which undermines security.
Troubleshooting Common SSL Errors
- “Your Connection is Not Private”: This common error can be caused by several issues: an expired certificate, a certificate issued for the wrong domain name (e.g., for
ded9.combut notwww.ded9.com), or a certificate from an untrusted CA. - Expired Certificate: SSL certificates have a finite lifespan. You must renew them before they expire to avoid security warnings and service interruptions.
- Mixed Content Warnings: Use your browser’s developer tools to identify and fix any resources that are still being loaded over HTTP.
Part 5: The Future of Web Security
The world of web security is constantly evolving to combat new threats.
- TLS 1.3: The latest version of the TLS protocol is faster and more secure than its predecessors. It simplifies the handshake process, reducing latency, and removes outdated, vulnerable cryptographic algorithms.
- Automation with ACME: The Automated Certificate Management Environment (ACME) protocol, pioneered by Let’s Encrypt, has revolutionized SSL deployment. It allows for the automated issuance and renewal of certificates, making HTTPS accessible to everyone, free of charge.
- Post-Quantum Cryptography: As quantum computers become more powerful, they pose a potential threat to current encryption standards. Researchers are actively developing new quantum-resistant algorithms to ensure data remains secure in the future.
Conclusion: Making Web Security a Priority
An SSL/TLS certificate is much more than a technical requirement; it’s a declaration of your commitment to your users’ privacy and security. It protects sensitive data, builds foundational trust, and is essential for visibility in the modern digital world. By understanding how SSL works, choosing the right certificate for your needs, and implementing it correctly, you are not just securing your website—you are contributing to a safer, more trustworthy internet for everyone.